Cybercriminals are always looking for new ways to bypass security defenses. That’s why it’s essential to think like a hacker […]
Cybersecurity is an essential aspect of any business or organisation. As technology evolves, so do the threats that can harm […]
Phishing scams remain one of the most prevalent and successful types of cyberattacks today, so being aware of the danger […]
While organisations and workers have certainly benefitted from the advancement of technology, it has also introduced an unprecedented number of […]
What You Should Know if Your Business Is Targeted by Ransomware It may not be news to you that ransomware […]
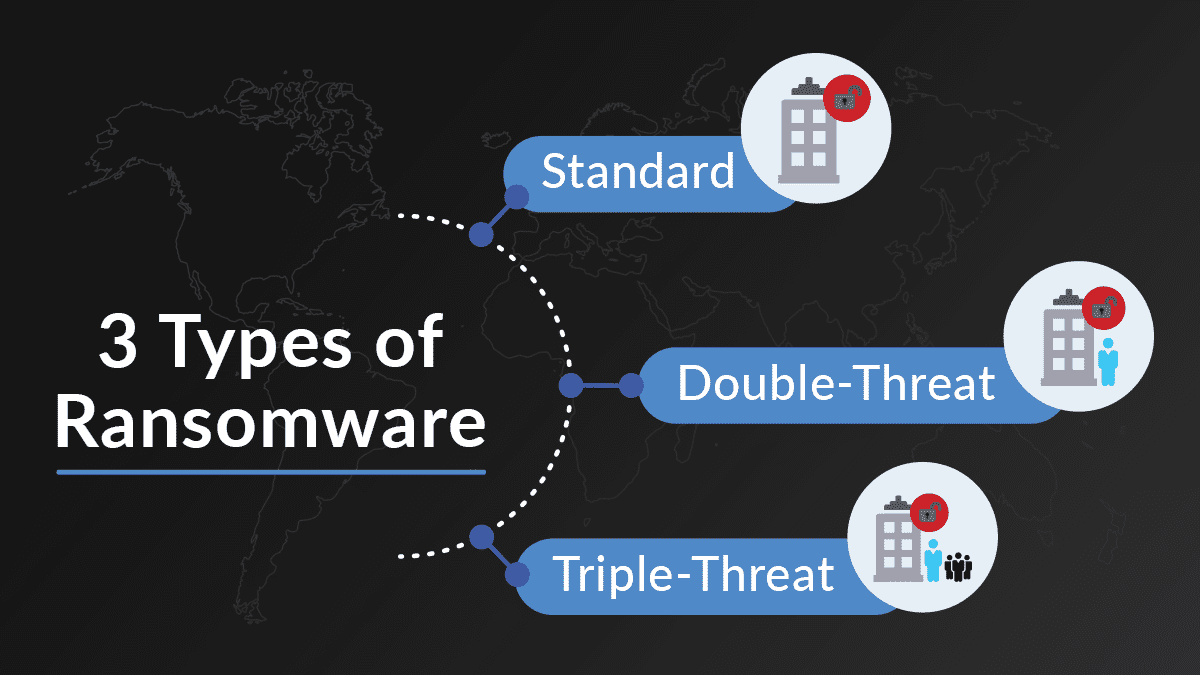
Think Beyond Basic Backups to tackle Ransomware Although ransomware has long been a serious concern for business owners all over […]
Top 7 Cybersecurity Risks of Remote Work & How to Address Remote work has become increasingly popular in recent times. […]
Handy Checklist for Handling Technology Safely During a Move Moving can be a chaotic and stressful time. Especially when it […]
What is Zero-Click Malware? Just How Do You Fight It? In today’s digital landscape, cybersecurity threats continue to evolve. They […]
Advantages of Adopting a Defense-in-Depth Cybersecurity Strategy Cybersecurity threats are becoming increasingly sophisticated and prevalent. In 2022, ransomware attacks jumped […]
How to Use Threat Modeling to Reduce Your Cybersecurity Risk As cyber threats continue to increase, businesses must take proactive […]
10 Tips for Small Businesses to be Ready for the Unexpected What would you do if your business suffered a […]
Business Email Compromise Jumped 81% Last Year! How to Fight It In recent years, electronic mail (email for short) has […]
9 NSA Best Practices for Securing Your Home Network In today’s world, technology is ubiquitous, and connectivity is a must. […]














Recent Comments